 5 minutes
5 minutes
The Payara Monthly Catch – January 2026
Published a little later than usual due to a busy conference season, this edition looks back at the key […]

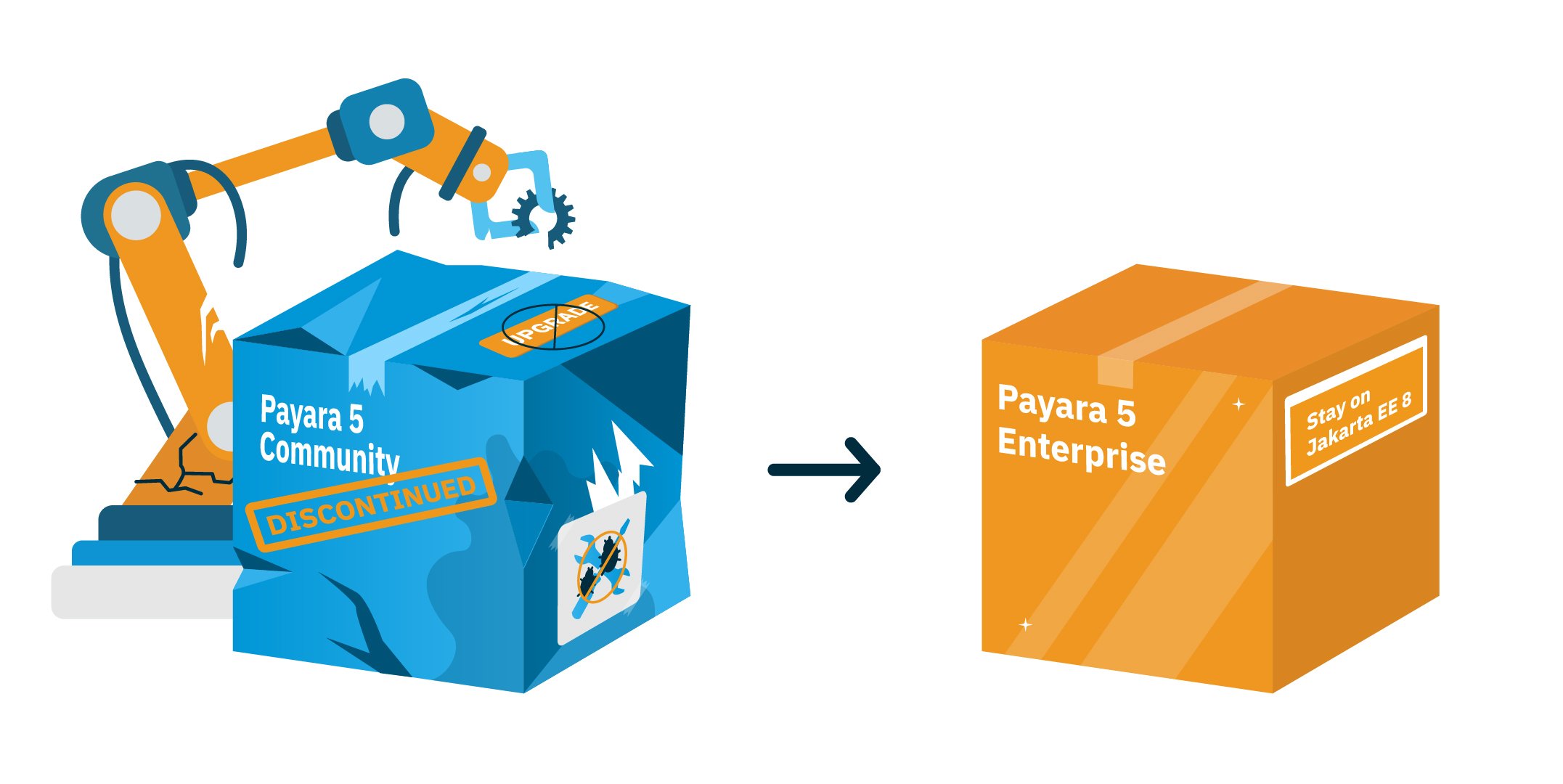
It’s the final release of the year and the final release of Payara 5 Community!
Payara Platform Community 6.2022.2 brings 20 component upgrades, 8 bug fixes, 2 security fixes and 4 improvements. Payara Platform Enterprise 5.46.0 brings 45 component upgrades, 13 bug fixes, and 2 security fixes.
Payara Platform Community 5.2022.5 is the final release of the Payara 5 Community stream.
All releases contain a key fix for a vulnerability in web applications deployed as the default module of an instance’s virtual server configuration. Read more details below!
You can request Payara Platform Enterprise 5.46.0 here.
You can download Community 6.2022.2 and 5.2022.5 here.
Payara 5 Community reaches its end this month. This final release is focused on clearing as many possible bugs as possible, and updating various components.
After this it will no longer be maintained; there will be no more bug fixes, component upgrades or improvements. In short, it will no longer be safe to use.
You must either:
Payara 5 Enterprise will continue to be supported as a Jakarta EE 8 certified runtime until 2028 for JDK 8 and JDK 17, and until 2026 for JDK 11. With Enterprise, you enjoy a 10-year software lifecyle alongside direct support from our engineers. Payara Enterprise will also include additional tooling and guidance to help you migrate your Jakarta EE 8 application to Jakarta EE 10 if and when you choose.
The December 2022 Payara Enterprise Release (request here) includes 45 component upgrades, 13 bug fixes, and 2 security fixes.
Payara Community 6.2022.2 (download here) includes 20 component upgrades, 8 bug fixes, 2 security fixes and 4 improvements.
Payara 5 Community’s final release (download here) includes 46 component upgrades, 12 bug fixes, 2 security fixes, and 2 improvements.
See a more detailed overview of the fixes and improvements in the Release Notes:
We received a report of a recent vulnerability that allows penetration attacks on web applications that are deployed as the default module of an instance’s virtual server configuration. The vulnerability in question allows attackers access to protected web resources that are guarded using standard Jakarta Authentication constraints.
If you deploy a web application on Payara Server under these conditions, you are affected, so please make sure to update your environments to use the latest released version to prevent any issues. If you do not use the default module configuration feature of web virtual servers in Payara Server, then there is no cause for immediate concern as this flaw will not affect you. Payara Micro is not affected by this vulnerability.
As usual, Payara Enterprise customers can request patch builds if upgrading their environments immediately is not an option.
Thank you to Luc Creti and Jean Michel Note, of Atos Group, for detecting this.
Download Payara Platform Here.
Share:
 5 minutes
5 minutes
Published a little later than usual due to a busy conference season, this edition looks back at the key […]
 4 minutes
4 minutes
Spring Framework 7 and Spring Boot 4 officially arrived, marking a key milestone for the Java ecosystem. From improved startup performance and modularization to native-image […]
 3 minutes
3 minutes
As we begin 2026, we’re pleased to announce new releases across all Payara Platform editions this January: Payara Platform […]